The Affiliate Fraud Bait-and-Switch: Using Device Intelligence to Unmask the New Generation of Sophisticated Affiliate Fraudsters
Discover how Bloomclicks Multilayered Fraud Guard uses Device Intelligence and Smart Signal Analysis to detect and block fraudulent clicks in real time. A critical wake-up call for every e-commerce merchant protecting their ad fraud prevention budget.

The Deception at Scale
Affiliate marketing still remains a core engine of the global e-commerce industry boom. By 2025, experts expect it to pull in over $17 billion worldwide. However, this performance-driven model has attracted a new and highly sophisticated adversary: the modern affiliate fraudster.
These affiliate fraudsters aren’t just spamming clicks anymore. They’re getting creative, using complex, layered schemes that strike deep at the very foundation of trust that performance marketing is known for.
The most dangerous of these new threats is the "Bait-and-Switch" scheme. This tactic is a calculated psychological and technical attack designed to bypass initial vetting and scale up the fraud exponentially.
The scheme begins with the affiliate sending a small, controlled volume of high-quality, genuine traffic (the Bait). This traffic exhibits perfect engagement metrics, easily passing conventional quality checks and convincing the advertiser that the source is legitimate.
Once the advertiser is assured and requests a significant budget or volume increase, the affiliate executes the Switch, flooding the system with massive amounts of cheap, automated, and fraudulent traffic.
The New Fraud Frontier: Why Initial Metrics Lie
For advertisers chasing optimizing ROI, a sudden surge in seemingly high-quality traffic from a new partner is a welcome sight. It feels like everything’s working; this positive feedback loop is precisely what the "Bait-and-Switch" relies on.
Traditional fraud detection systems often focus solely on the quality of a lead after conversion or rely on basic IP blacklisting, which are methods easily circumvented. By the time a merchant realizes their ROI has plummeted and their conversion data is polluted, they have already paid out commissions on fake traffic, often for months.
Current Statistics & Data: Establishing the Unprecedented Threat
The financial toll of these sophisticated schemes illustrates why ad fraud prevention is no longer optional.
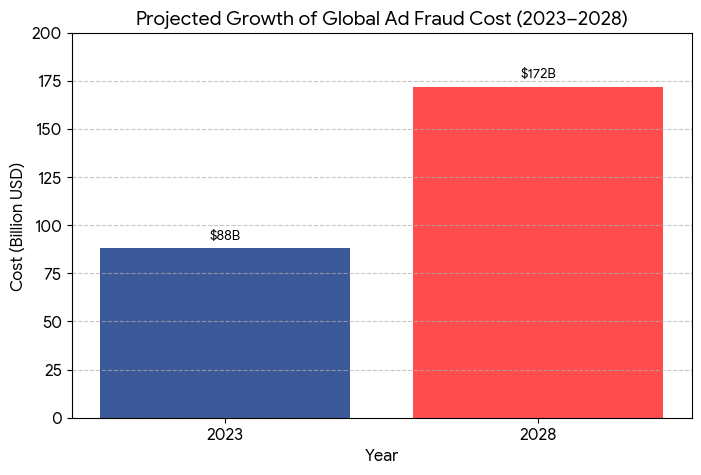
- Global Financial Drain: The global cost of ad fraud is predicted to rise from an estimated $88 billion in 2023 to a staggering $172 billion by 2028 (Statista/Juniper Research), much of which involves sophisticated invalid traffic (IVT) like that found in affiliate programs.
- Affiliate Channel Specifics: Some industry reports suggest that up to 30% of all affiliate marketing losses are tied to fraud, with affiliate networks losing billions annually.
- Hidden Costs: But the real damage isn’t just in wasted commission fees. These fake clicks and leads seep into your campaign data, messing up analytics and sending your marketing budget in the wrong direction. You pay for actions that aren’t real, and meanwhile, your true cost to get real customers quietly climbs.
This is a wake-up call for e-commerce merchants and advertisers everywhere: your current fraud models are being intentionally weaponized against you. Exposing this new generation of sophisticated affiliate fraudsters requires moving beyond conventional metrics and into the realm of technical analysis.
Understanding the Fraudster’s Playbook
The success of the Bait-and-Switch relies on precision and technical cloaking. The modern affiliate fraudster operates like a seasoned cybercriminal, using advanced infrastructure to mimic human behaviour just long enough to collect a large payout. Understanding their four-stage playbook is the first step toward effective affiliate fraud detection.
The Four Stages of the Bait-and-Switch Attack
Phase I: The Trust Baseline (The Bait): The fraudster delivers a small volume of traffic using legitimate, clean methods, often real devices or high-quality residential proxies. The goal is to establish a trusted performance marketing record, with low bounce rates and a genuine (but low) conversion rate. This traffic passes all automated filters.
Phase II: The Budget Request: Armed with months of pristine, yet limited, data, the affiliate successfully persuades the advertiser to significantly increase the campaign budget and traffic volume.
Phase III: The Deployment (The Switch): The affiliate flips the switch. To meet the massive volume requirement, they deploy large-scale fraud, often driven by botnets, emulators, or virtual machines. They flood the system with low-cost, automated clicks and impressions, generating high commissions instantly.
Phase IV: The Cover-Up: The fraud is often routed through sophisticated TCP tunnels or custom proxy networks. These methods mask the true data center origin of the bot traffic, making it appear to come from diverse, residential IP addresses—a deliberate effort to defeat standard IP-based ad fraud detection tools.
The Technical Fingerprints of New Fraud
Our analysis at Bloomclicks Multilayered Fraud Guard found that even the most advanced affiliate fraud detection schemes leave telltale technical fingerprints at the click level:
- Identical Fingerprints of Fraud: The genuine "Bait" traffic shows vast diversity in device types, operating systems, and browser configurations. The fraudulent "Switch" traffic, however, exhibits identical fingerprints across thousands of clicks. This uniformity, same screen resolution, same font lists, same CPU core count—is impossible for genuine human traffic and instantly flags an automated script or a massive cluster of cloned virtual machines.
- Click Flooding and Prodding: Automated systems generate clicks with unnatural, machine-like precision. Click flooding and prodding (repetitive, timed interactions) generate clicks at a velocity or frequency that no human user could possibly sustain, manipulating the Cost Per Click (CPC) and the impression data.
- Automated CPC Manipulation via TCP Tunnel: The use of TCP tunnels allows fraudsters to obscure the bot network's true identity, preventing basic IP blocking. However, the traffic remains homogenous and displays the characteristic low-level signals of automation when subjected to Device Intelligence analysis. This technical exposure of the cloaking layer is crucial for effective performance marketing fraud prevention.
| Traffic Type | Key Technical Fingerprint | Detection Insight |
| Fraudulent Traffic (The "Switch") | Identical Device Fingerprints | Indicates a cluster of cloned Virtual Machines (VMs) or emulators, which is impossible for genuine human users. |
| Click Flooding & Prodding | Reveals inhuman, machine-like velocity and mechanical timing of clicks. | |
| TCP Tunnel Cloaking | Hides the data center origin, but the traffic still exposes generic, non-residential technical signals. | |
| Genuine Traffic (The "Bait") | Diverse Device Fingerprints | Shows the expected natural variety in OS, browser, screen resolution, and font lists. |
| Natural, Varied Click Behavior | Exhibits organic, erratic, and human-paced interactions. | |
| Organic, Intent-Driven Interactions | Clicks are aligned with meaningful actions and longer session durations. |
The Bloomclicks Multilayered Defense (The Solution)
The fundamental flaw in traditional affiliate fraud detection is that it is often reactive, relying on retrospective analysis of low conversion rates or a high volume of chargebacks. To defeat the Bait-and-Switch, where the fraud is cloaked by initial good traffic, prevention must be proactive, analyzing the quality of every single click at the deepest technical level.
This is the principle behind the Bloomclicks Multilayered Fraud Guard. Our solution moves beyond IP addresses and simple rules to leverage a synergistic approach of Device Fingerprinting, Device Intelligence, and Smart Signal Analysis, stopping large-scale fraud while it is still in the clicking phase.
Stopping Fraud at the Click: Bloomclicks’ Unique Edge
Traditional methods fail because they are designed to catch simple bots. The new generation of fraudsters uses sophisticated virtual machines (VMs) and TCP tunnels to emulate real users. The only way to expose this is by examining the hidden technical attributes that even the most advanced cloaking software cannot perfectly replicate.
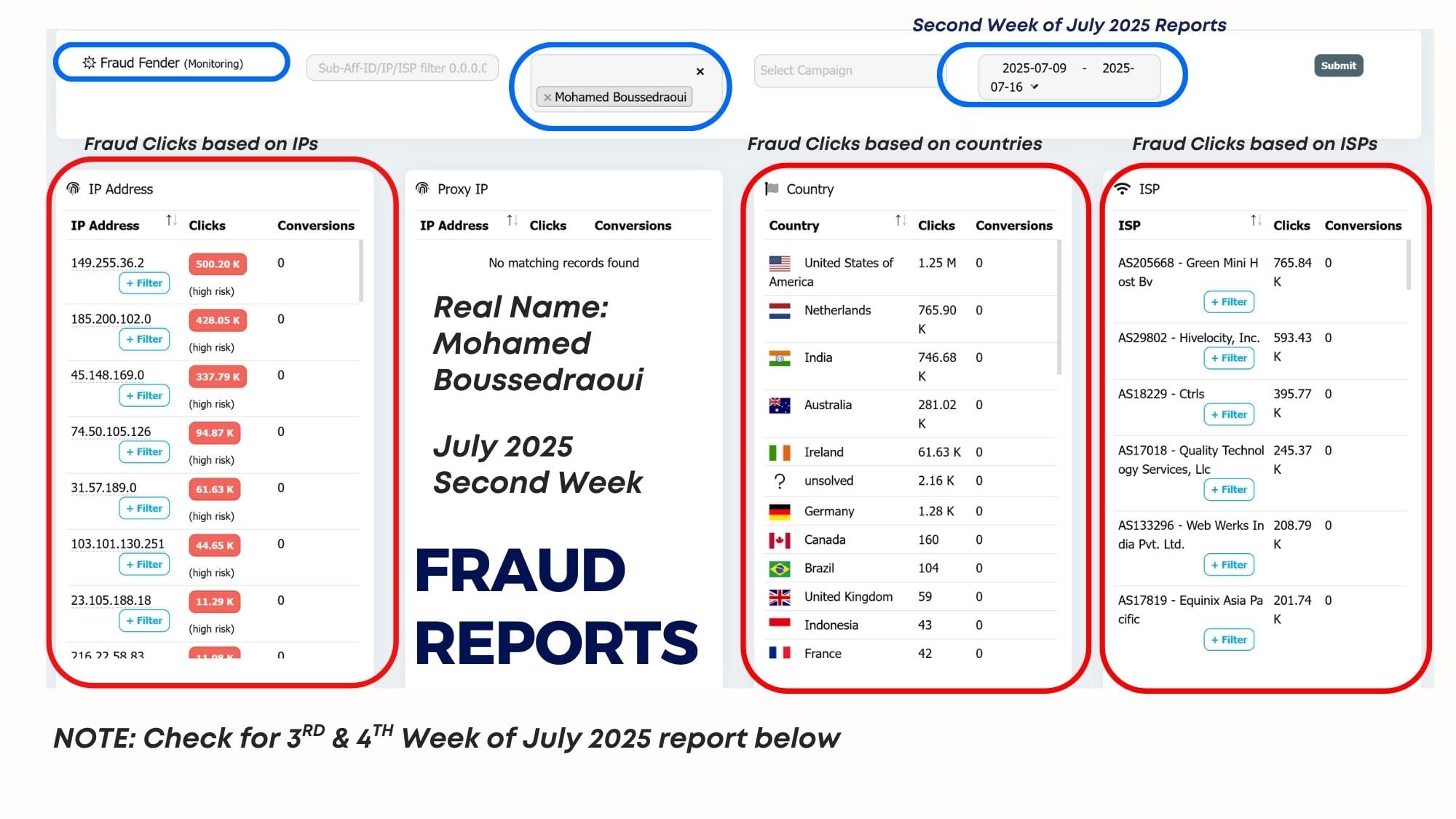
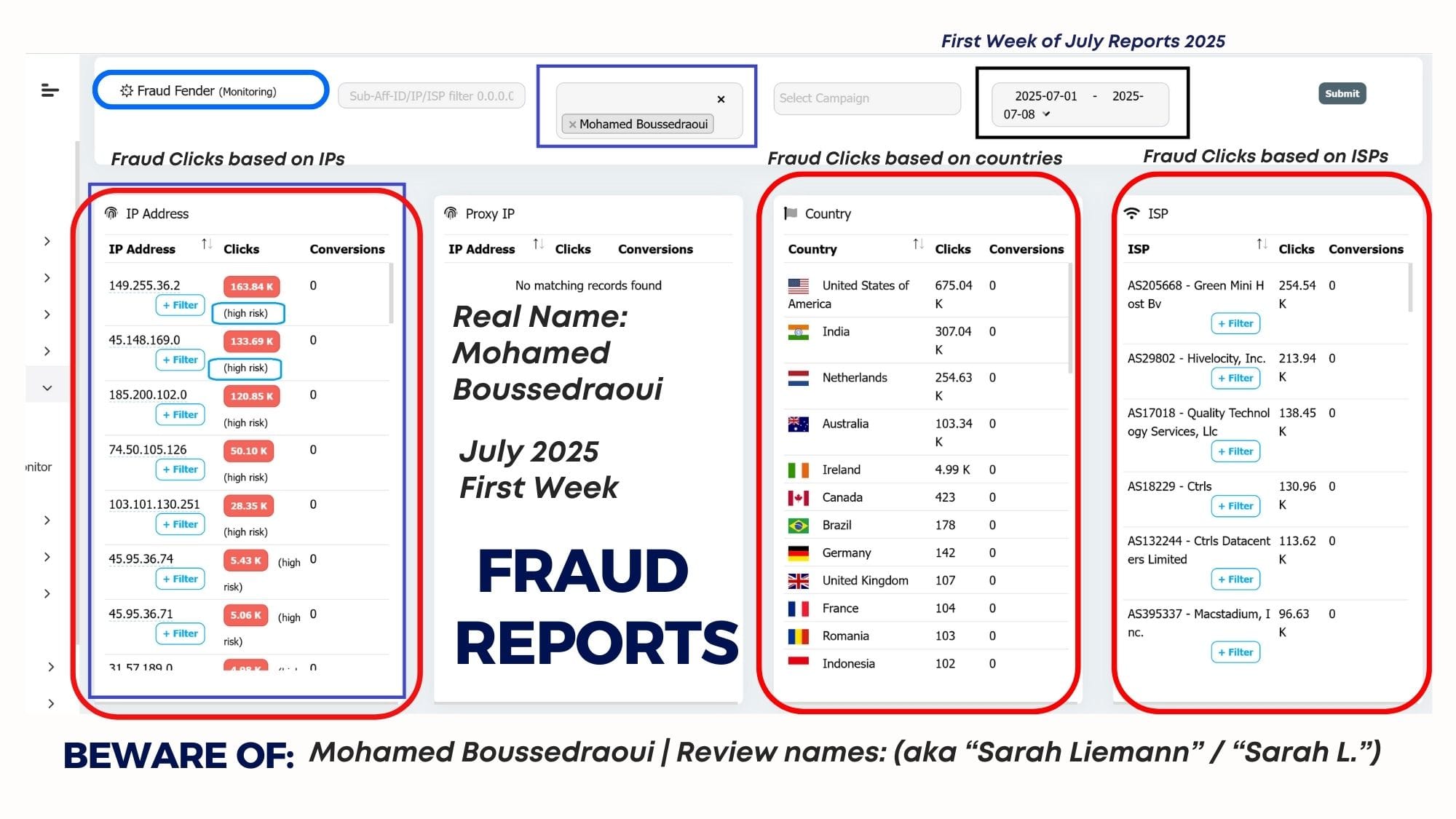
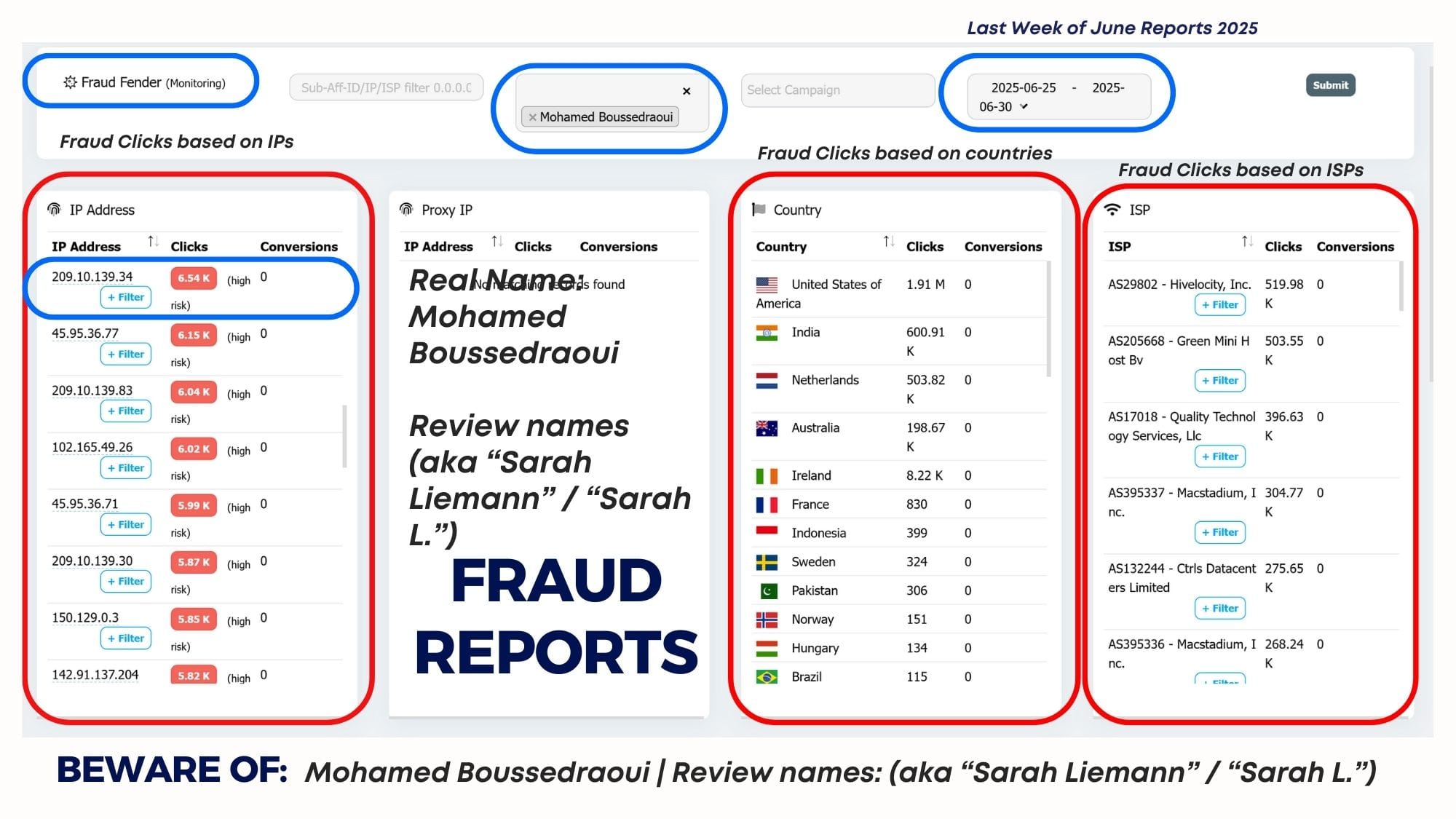
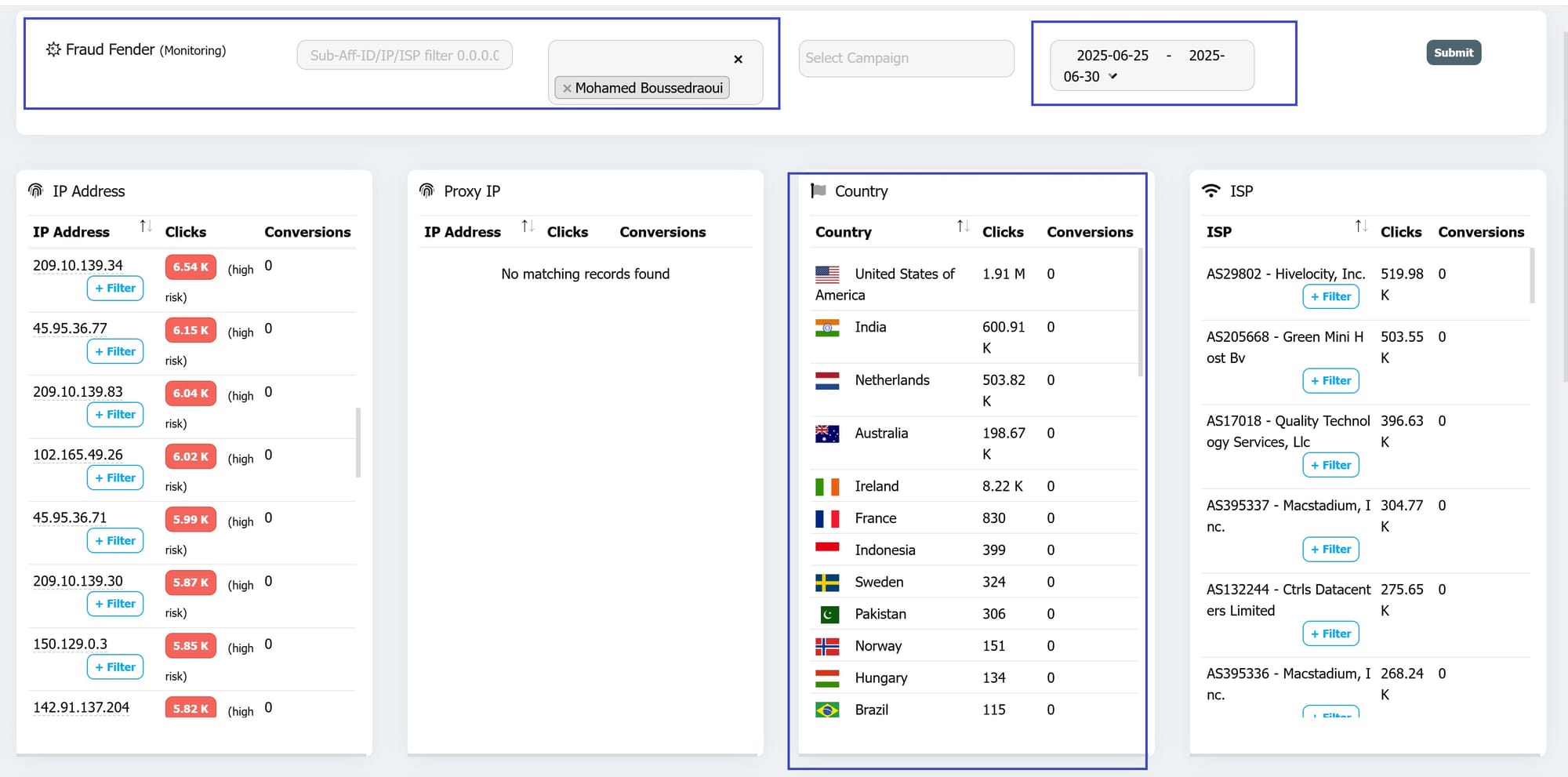
Stopping fraud at the click levelE
Bloomclicks established that the massive spike in traffic—the "Switch"—was indeed automated by identifying identical fingerprints and the telltale signs of click flooding and prodding that signal automation:
- Identical Fingerprints: While the initial legitimate traffic showed a natural, diverse mix of device profiles, the scaled traffic exhibited suspicious uniformity. Thousands of clicks shared the exact same set of technical attributes: matching OS versions, browser headers, screen resolutions, and even the same list of installed fonts, indicating a large cluster of cloned devices or emulators.
- Prodding and Click Velocity: The traffic showed inhuman behaviour: clicks occurring with mechanical precision (prodding) and at speeds that exceeded any physical or human capacity (click flooding), all designed to artificially inflate impression and click counts to manipulate the CPC.
- Exposing the TCP Tunnel: The TCP tunnel masks the fraud's origin, making it appear as clean residential traffic. However, the Device Intelligence layer penetrated this cloaking, revealing that the highly consistent, high-velocity clicks were still originating from machine-controlled, non-human environments.
The Technical Pillars of Device-Level Prevention
Our Multilayered Fraud Guard operates on three core technical pillars that dismantle the fraudster’s cloaking efforts:
A. Device Fingerprinting: The Unforgeable ID
This is the foundation. It pulls in hundreds of non-PII (Personally Identifiable Information) data points straight from the user’s browser and operating system; this includes WebGL rendering data, font lists, and hardware configurations. All these combine to build a unique, persistent device hash. Faking this fingerprint? Nearly impossible. So when you ask, “Is this the same device we’ve seen before?” this method gives you a clear answer.
B. Device Intelligence (DI): The Contextual Brain
DI takes the raw fingerprint data and applies complex logic and machine learning to add context. It looks for inconsistencies that human users would never generate:
- Emulator/VM Detection: Directly identifying signatures of Virtual Machines or Emulators commonly used to automate mobile app clicks.
- Network Mismatches: Flagging traffic where a device's system time or language is completely inconsistent with its geographic IP location.
- Behavioral Anomaly Detection: Recognizing the difference between a bot’s suspiciously perfect mouse movement or form-fill time versus the erratic, natural human interaction.
C. Smart Signal Analysis: Real-Time Risk Scoring
This layer synthesizes all data into an actionable risk score. It uses the characteristics of the trusted, legitimate traffic (the "Bait") to train an AI model.
When the volume scales, the system can instantly compare new traffic against this trusted baseline. Any click that triggers multiple negative Smart Signals (e.g., High Click Velocity + Emulator Detected + Uniform Fingerprint) is assigned a critical score and is blocked in real-time before commission is paid. This prevents the vast majority of the "Switch" traffic from ever contaminating the advertiser's funnel.
A Wake-Up Call for E-commerce Merchants and Advertisers
The successful detection of the Bait-and-Switch scheme is a critical validation of Device Intelligence technology, but it must also serve as a stark warning to e-commerce merchants and advertisers. The risk is no longer just commissions paid; it is the total breakdown of trust and data integrity.
The Merchant Risk: Beyond Commission Payouts
Fraud goes far beyond just eating up your ad budget. The real damage runs deeper:
- Bad Data, Wasted Money: Every fake click, every bot-driven session, all of it muddies your analytics. Suddenly, you’re making decisions about retargeting, channel spending, and audience profiles based on junk data. Advertisers end up throwing good money after ghosts—chasing customers who aren’t even real.
- Erosion of Brand and Partner Trust: High volumes of low-quality traffic strain relationships with ad networks and media partners. Worse, if the fraud leads to transactions using stolen credit cards, the merchant faces increased chargeback risk and penalties from payment processors.
- Inflated Customer Acquisition Cost (CAC): When commissions are paid on fake leads, the reported CAC is artificially deflated by the successful "Bait" phase, only to skyrocket once the "Switch" traffic fails to convert, leading to inaccurate financial forecasting.
The Cost of Integrity: Fraudster Retaliation and False Narratives
Note to the Public:
Exposing organized fraud of this magnitude is not without consequences. As documented in our case study screenshots , the affiliates caught attempting this large-scale scam have resorted to personal and aggressive retaliation.
This includes calling our team unprintable names and attempting to discredit our technology by leaving false reviews and narratives on social media and other public forums.
This behaviour attacking the very tools designed to protect advertisers, is proof of the financial threat our new inventions pose to their fraudulent business model and serves as an unfortunate measure of our effectiveness. We urge the general public to consider the source and intent behind any such unsubstantiated claims.
Three Immediate Action Steps for Advertisers
To safeguard your performance marketing budgets against these advanced threats, advertisers must take decisive action:
- Stop Blindly Scaling: Implement a "Quality-Gate" Scale-Up Policy. Never authorize a large volume increase based on initial, small-scale performance alone. Require a mandatory secondary audit using Device Intelligence tools to verify the diversity and integrity of the traffic before signing off on a major budget boost.
- Mandate Technical Transparency: Update affiliate contracts to demand access to full click logs and technical signals (browser attributes, device hashes, timestamp data) for audit. Make it a contractual breach to obscure traffic origin using methods like TCP tunnels or non-approved proxies.
- Invest in Pre-Emptive, Click-Level Prevention: Move away from relying on post-conversion checks. Fraud must be stopped at the click. Require partners to integrate with third-party affiliate fraud detection platforms that use Device Intelligence and Smart Signal Analysis to score traffic risk in real-time, blocking bad clicks before they impact your servers or wallet.
Collective Action for Industry Resilience
The way Bait-and-Switch scams keep evolving shows one thing: fighting ad fraud isn’t a solo sport. No single company can keep up on its own. The industry needs to band together, share intelligence, set standards, and build defences as a group. That’s the only way to stay ahead.
Standardizing Fraud Data & Definitions
Progress in fraud reduction in the partnership industry has historically been driven by industry bodies like TAG (Trustworthy Accountability Group), IAB, and the MRC. But this required continued effort collectively:
- Universal IVT Taxonomy: We need to further standardize the definition of Invalid Traffic (IVT) to explicitly include advanced tactics like "test traffic misrepresentation" and "cloaked TCP tunnel usage" so there’s no grey area.
- Shared Threat Intelligence: The industry needs more effort to establish protocols for Device Intelligence vendors to safely share anonymized data on malicious device fingerprints and high-risk IP clusters associated with coordinated affiliate fraud schemes. By pooling this data, the industry creates a strong network effect, detecting fraud patterns faster and effectively across multiple merchants simultaneously.
Conclusion: The affiliate channel is an invaluable resource, but advertisers must recognize that sophisticated, financially motivated organized crime is now operating within it, as has been established by our new system. The exposed Affiliate Fraud Bait-and-Switch scheme is a clear signal, although it is only one of many. It is imperative your anti-fraud defences must evolve from simple filtering to multilayered Device Intelligence.
By prioritizing technical transparency and implementing pre-emptive real-time click-level prevention, and by standing firm against the retaliation of exposed fraudsters, the industry can protect its data, its budgets, and its integrity for years to come.